About Us
Executive Editor:Publishing house "Academy of Natural History"
Editorial Board:
Asgarov S. (Azerbaijan), Alakbarov M. (Azerbaijan), Aliev Z. (Azerbaijan), Babayev N. (Uzbekistan), Chiladze G. (Georgia), Datskovsky I. (Israel), Garbuz I. (Moldova), Gleizer S. (Germany), Ershina A. (Kazakhstan), Kobzev D. (Switzerland), Kohl O. (Germany), Ktshanyan M. (Armenia), Lande D. (Ukraine), Ledvanov M. (Russia), Makats V. (Ukraine), Miletic L. (Serbia), Moskovkin V. (Ukraine), Murzagaliyeva A. (Kazakhstan), Novikov A. (Ukraine), Rahimov R. (Uzbekistan), Romanchuk A. (Ukraine), Shamshiev B. (Kyrgyzstan), Usheva M. (Bulgaria), Vasileva M. (Bulgar).
Materials of the conference "EDUCATION AND SCIENCE WITHOUT BORDERS"
The task of ensuring security on the Internet is not only about ensuring the security of individual users, but also the security of the state as a whole. Practically uncontrolled growth of the amount of resources and volume of information every day, make it difficult to monitor and identify the resources and information posing a threat [1]. Social networks are one of the sources of emergence and spread threatening information.
Often the moderation of posts in social networks is reduced to the search for such violations as placing off topic posts and comments, containing advertising information, but such messages may contain such violations as calls for incitement of ethnic hatred, discussion and organization of anti-social activities, etc [2].
The social network architecture
In the article the authors discuss the development of architecture for a multi-agent subsystem analyzing user posts in social networks in order to identify security threats to society. Network for blogging is selected as a social network [1]. The social network architecture is shown in Fig. 1.
Social network consists of two subsystems:
· Subsystem for working with users,
· Subsystem for user posts analyzing.
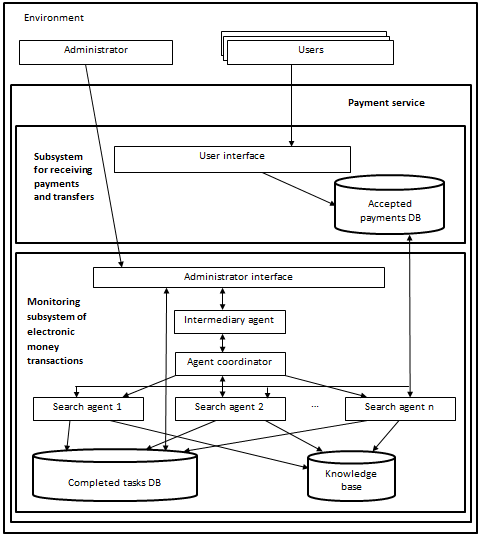
Fig. 1. The social network architecture
Subsystem for user posts analyzing. Agents
The subsystem includes the administrator interface through which a human-administrator forms tasks that fall to the intermediary agent and after completion of all the tasks he can view the results in completed tasks database.
An intermediary agent interprets requests from human-administrator to the internal language of agents, and sends them to agent coordinator. When the intermediary agent receives a message from an agent coordinator about the completion of all the tasks it transmits a human-administrator the message in natural language.
The agent coordinator is responsible for the allocation of duties between the agents and their communication. After receiving interpreted requests the agent coordinator analyzes its volume and in the case if the volume is too large, it allocates tasks between several search agents. When the agent coordinator receives a signal of the task end from the last search agent it sends a message to the intermediary agent.
After getting the task a search agent [3] accesses the social network database, analyzes the volume of works, comparing the previous state of the database with the current, selects the action to be performed (scanning, checking on certain parameters), analyses contained entries on the subject of the presence of threats to society. The analysis is carried out on the basis of the ontology contained in the knowledge base. At the end of the process all the results are entered in the completed tasks database. Search agents report of the tasks end to agent coordinator. The search agent model is shown in Fig. 2.
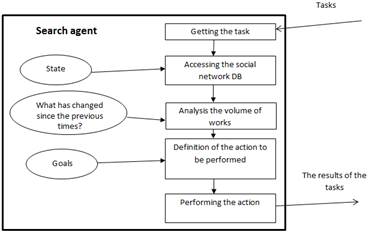
Fig. 2. The search agent model
Conclusions
The authors developed architecture for a multi-agent subsystem analyzing user posts in social networks in order to identify security threats to society, presented the models of agents and scripts of their behavior. Thanks to the multi-agent approach most of the routine tasks are delegated to the agents, the moderation process becomes easier and more efficient.
2. Okhapkina E.P. Materialy 5 mezhdunarodnoj nauchno-prakticheskoj konferencii "Social'no-antropologicheskie problemy informacionnogo obshhestva" (Proc. 5th International scientific and practical conference "Social and anthropological issues of the information society"). Kirov 2011, pp.102-105.
3. Russell S. and Norvig P. Artificial Intelligence: A Modern Approach (1995), Available at: http://stpk.cs.rtu.lv/sites/all/files/stpk/materiali/MI/Artificial%20Intelligence%20A%20Modern%20Approach.pdf
Okhapkina E.P, Voronova L.I. THE DEVELOPMENT OF ARCHITECTURE FOR A MULTI-AGENT SUBSYSTEM ANALYZING USER POSTS IN SOCIAL NETWORKS IN ORDER TO IDENTIFY SECURITY THREATS TO SOCIETY. International Journal Of Applied And Fundamental Research. – 2013. – № 2 –
URL: www.science-sd.com/455-24392 (17.12.2025).










 PDF
PDF